MMS redownload and group MMS
-
Hello @jezek and @lduboeuf
I have a (new ?) question about the mechanism :Is the mms redownload mechanism supposed to work in the case of sending a group mms (androïd phone) by a sender to several recipients? In my case (under Xenial) and on two different sendings by a sender, I could not recover the mms which were intended for me whereas to check, the sending of an mms to myself worked well.
Thanks in advance for the clarification. -
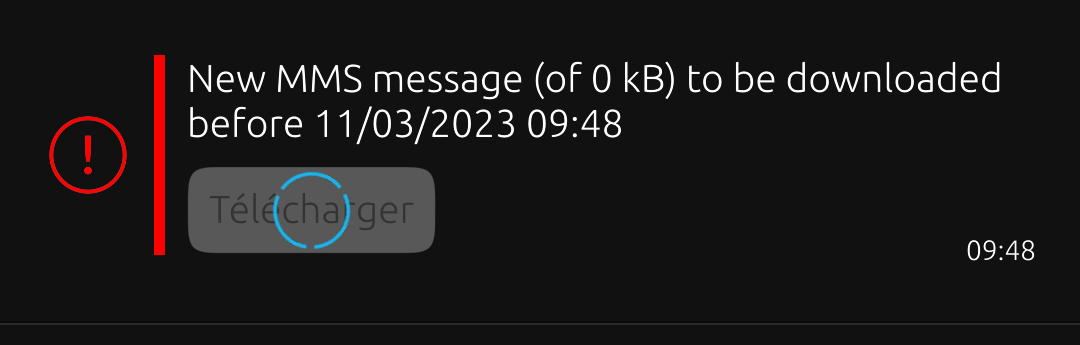
Confirmation: the grouped mms to be recovered is marked 0 KB and cannot be recovered, while a classic mms has XX KB and can be recovered.
-
@domubpkm
AFAIK, MMS Group has never worked well on UT -
@lduboeuf In fact I don't know if it works or not in simple reception of a grouped MMS, but in any case the recovery does not work in my attempts.
-
@domubpkm Could you provide logs ?
If on 16.04nuntium.login .cache//upstart or on 20.04sudo journalctl --since "2023-03-XX" --until "2023-03-XX" | grep nuntium -
@lduboeuf
A looping excerpt.
If you want to see the full log, I won't post it here.
-
@domubpkm yes nothing usefull. Need to have more complete logs ( beware phone-numbers there )
-
As much I remember, the group MMS gets received by nuntium with success, nuntium then sends the message to telepathy-ofono and there it gets lost.
I wrote somewhere (I really can't recall where, maybe I just thougt it to myself) that a dirty hotfix would be just handle the group mms as a single mms (with a note somewhere, that it was a group mms before) and it will be at least delivered.
The 0 kB size can be a small error in MNotification.Ind (PDU) decoding, I spotted when poking around nuntium lately. The merge request is a work in progress right now.
-
This post is deleted! -
-
@domubpkm said in MMS redownload and group MMS:
00000000 00 06 07 be bx 72 8d df b4 81 8c 82 98 41 75 43 |.............AuC|
00000010 49 4a 35 56 61 48 53 00 8d 92 89 16 60 2b 33 33 |Iy5faPS......+33|
00000020 36 31 35 32 32 35 39 31 34 2f 54 59 40 45 2d 50 |*********/TYPE=P|
00000030 4c 4d 4e 00 86 81 8a 80 8e 02 0b 18 88 05 81 03 |LMN.............|
00000040 03 f4 80 83 41 74 74 70 3a 2f 2f 76 6d 32 2e 62 |....http://vg3.b|
00000050 79 71 65 6c 2e 64 72 2f 6d 6d 73 63 2f 3f 40 75 |ytel.fr/mmsc/?Au|
00000060 43 45 7a 35 56 61 51 50 01 |CIz5VaPJ.|I tried to use this m-notification.ind in tests, but it seems the numbers were randomly modified. Can you send me (eg. via PM) the unedited data please, I would like to include it in tests (after anonymizing it a little bit). Thanks.
-
Hello @jezek . Sorry, I didn't keep the original nuntium and I very regularly erase all the cache of my Volla so no more nuntium..
If I ever receive a new failed grouped mms, I will think about that. Regards -
@domubpkm It doesn't have to be failed group multimedia message. Any from your operator+country will do. There is currently close to zero testing data right now for decoding PDUs, so it would be only good to collect some m-notification.ind for a few countries & operators to get some testing data from real world. It would benefit future development. It is always good to know if you broke some tests with code changes.
So if anyone wants to help, you could send me some of those log chunks after receiving a multimedia message. Beware, there is a phone number encoded inside, so restrain from posting public, if you care for privacy.
-
@jezek said in MMS redownload and group MMS:
there is a phone number encoded inside, so restrain from posting public, if you care for privacy.
do you mean you need the data with the phone numbers ??
-
D domubpkm marked this topic as a regular topic on
-
@domubpkm said in MMS redownload and group MMS:
do you mean you need the data with the phone numbers ??
No, I don't need the phone numbers nor any private data. You can edit it out.
But beware, do not edit random numbers from the middle number part. It is a hex dump and some data is there encoded twice.
Let's say, we have a hexdump from logs like this:
00000000 01 06 26 61 70 70 6c 69 63 61 74 69 6f 6e 2f 76 |..&application/v| 00000010 6e 64 2e 77 61 70 2e 6d 6d 73 2d 6d 65 73 73 61 |nd.wap.mms-messa| 00000020 67 65 00 af 84 b4 86 c3 95 8c 82 98 6d 30 34 42 |ge..........m04B| 00000030 4b 6b 73 69 6d 30 35 40 6d 6d 73 2e 70 65 72 73 |Kksim05@mms.pers| 00000040 6f 6e 61 6c 2e 63 6f 6d 2e 61 72 00 8d 90 89 19 |onal.com.ar.....| 00000050 80 2b 35 34 33 35 31 35 39 32 34 38 30 36 2f 54 |.+543515924806/T| 00000060 59 50 45 3d 50 4c 4d 4e 00 8a 80 8e 02 74 00 88 |YPE=PLMN.....t..| 00000070 05 81 03 02 a2 ff 83 68 74 74 70 3a 2f 2f 6c 6f |.......http://lo| 00000080 63 61 6c 68 6f 73 74 3a 39 31 39 31 2f 6d 6d 73 |calhost:9191/mms| 00000090 00 |.|The phone number is encoded in the string
+543515924806, but also in2b 35 34 33 35 31 35 39 32 34 38 30 36in the same line.Soif you wan to anonymize the phone number into e.g.
+123456789012then you have to change the middle part into2b 31 32 33 34 35 36 37 38 39 30 31 32and the resulting hexdump from logs would be:00000000 01 06 26 61 70 70 6c 69 63 61 74 69 6f 6e 2f 76 |..&application/v| 00000010 6e 64 2e 77 61 70 2e 6d 6d 73 2d 6d 65 73 73 61 |nd.wap.mms-messa| 00000020 67 65 00 af 84 b4 86 c3 95 8c 82 98 6d 30 34 42 |ge..........m04B| 00000030 4b 6b 73 69 6d 30 35 40 6d 6d 73 2e 70 65 72 73 |Kksim05@mms.pers| 00000040 6f 6e 61 6c 2e 63 6f 6d 2e 61 72 00 8d 90 89 19 |onal.com.ar.....| 00000050 80 2b 31 32 33 34 35 36 37 38 39 30 31 32 2f 54 |.+123456789012/T| 00000060 59 50 45 3d 50 4c 4d 4e 00 8a 80 8e 02 74 00 88 |YPE=PLMN.....t..| 00000070 05 81 03 02 a2 ff 83 68 74 74 70 3a 2f 2f 6c 6f |.......http://lo| 00000080 63 61 6c 68 6f 73 74 3a 39 31 39 31 2f 6d 6d 73 |calhost:9191/mms| 00000090 00 |.| -
@jezek Thank you for your explanation but sorry, all this sharp formatting work is not work for me. It will probably be helpful to others being able to help you.
Good luck in your future developments.