Using GnuPG in the UbuntuPhone BQ E4.5 (part1: GnuPG)
-
Using GnuPG-card in the UbuntuPhone BQ E4.5:
Create a complete Linux system into ~phablet/myRoot/ :
phablet@ubuntu-phablet-bq:~$ mkdir myRoot phablet@ubuntu-phablet-bq:~$ cd myRoot phablet@ubuntu-phablet-bq:~$ sudo tar xzf ubports-touch.rootfs-xenial-armhf.tar.gz phablet@ubuntu-phablet-bq:~$ sudo chroot myRoot/Install additional packages into the Linux system:
root@ubuntu-phablet:/# apt-get install pinentry-curses root@ubuntu-phablet:/# apt-get install pass root@ubuntu-phablet:/# apt-get install libudev-dev root@ubuntu-phablet:/# apt-get install gcc root@ubuntu-phablet:/# apt-get install libc-dev root@ubuntu-phablet:/# apt-get install makecompile in myRoot the following pieces (in the given order):
libgpg-error-1.33 libassuan-2.5.1 libksba-1.3.5 npth-1.6 libgcrypt-1.8.4 gnupg-2.2.12always with
./configure && make && sudo make install; the software ends
up below/usr/local(which is/home/phablet/myRoot/usr/localwhen one looks from outside the chroot'ed phone system);note:
gpg2is/usr/local/bin/gpgNow from the phone system configure:
$ mkdir ~/.gnupg $ chmod 0700 ~/.gnupg $ cat .gnupg/gpg.conf # agent-program /home/phablet/myRoot/usr/local/bin/gpg-agent $ cat .gnupg/gpg-agent.conf pinentry-program /home/phablet/myRoot/usr/bin/pinentry-curses scdaemon-program /home/phablet/myRoot/usr/local/libexec/scdaemon log-file /home/phablet/gpg-agent.log log-file /dev/null debug-level guru max-cache-ttl 10Due to the nature of the installation in the chrooted system we
need small wrapper scripts to setPATH, LD_LIBRARY_PATH, ...and
other stuff;$ cat ~/gpg.sh #!/bin/sh LD_LIBRARY_PATH=/home/phablet/myRoot/usr/local/lib export LD_LIBRARY_PATH PATH=/home/phablet/myRoot/usr/local/bin:$PATH export PATH GNUPGHOME=/home/phablet/.gnupg export GNUPGHOME GPG_TTY=$(tty) export GPG_TTY /home/phablet/myRoot/usr/local/bin/gpg-agent \ --homedir /home/phablet/.gnupg \ --daemon \ --pinentry-program /home/phablet/myRoot/usr/bin/pinentry-curses /home/phablet/myRoot/usr/local/bin/gpg-connect-agent /bye /home/phablet/myRoot/usr/local/bin/gpg $*run and create for test a keypair (later we want to use the GnuPG-card
for this)$ ~/gpg.sh --full-generate-key gpg-agent[2973]: enabled debug flags: mpi crypto memory cache memstat hashing ipc gpg (GnuPG) 2.2.1; Copyright (C) 2017 Free Software Foundation, Inc. This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Please select what kind of key you want: (1) RSA and RSA (default) (2) DSA and Elgamal (3) DSA (sign only) (4) RSA (sign only) Your selection? ...This starts the gpg-agent as:
$ ps ax | grep gpg-a 2974 ? Ss 0:00 /home/phablet/myRoot/usr/local/bin/gpg-agent --homedir /home/phablet/.gnupg --daemon --pinentry-program /home/phablet/myRoot/usr/bin/pinentry-cursesNow we can use the the
passcommand we installed in the chroot'es system with$ cat pass.sh #!/bin/sh LD_LIBRARY_PATH=/home/phablet/myRoot/usr/local/lib export LD_LIBRARY_PATH PATH=/home/phablet/myRoot/usr/local/bin:$PATH export PATH GNUPGHOME=/home/phablet/.gnupg export GNUPGHOME GPG_TTY=$(tty) export GPG_TTY unset GPG_AGENT_INFO /home/phablet/myRoot/usr/bin/pass $*Init the pass storage as:
$ ./pass.sh init Matthias Password store initialized for Matthias web/bla: reencrypting to A62DCD2809AC14F6 $ find .password-store/ .password-store/ .password-store/.gpg-idInsert some password for test:
$ ./pass.sh insert -m web/bla Enter contents of web/bla and press Ctrl+D when finished: password-bla Username: guru$ ./pass.sh web/bla ┌────────────────────────────────────────────────────────────────┐ │ Please enter the passphrase to unlock the OpenPGP secret key: │ │ "Matthias Apitz (test) <guru@sisis.de>" │ │ 2048-bit RSA key, ID 93A6FBF52FA76DB0, │ │ created 2017-09-22 (main key ID 3FECB79DDDA409E4). │ │ │ │ │ │ Passphrase: ***_______________________________________________ │ │ │ │ <OK> <Cancel> │ └────────────────────────────────────────────────────────────────┘ password-bla Username: guruWe now can use
gpg2andpassdirectly in the phone to have always our secrets, PIN's etc. with us.I have here two screen-shots, taken of the terminal-app: In the 1st I have typed in the command
./pass.sh web/fooasking for the (cleartext) values ofweb/foo(which could be your bank account, login credentials or whatever you can think of). The result visible in this screen (xxx yyy) is only shown after entering the passphrase to unlock your GnuPG secret key, see screen 2. The key is 4096 bits RSA. The key store remains 10 seconds (configurable) unlocked, after which you're asked again for the passphrase.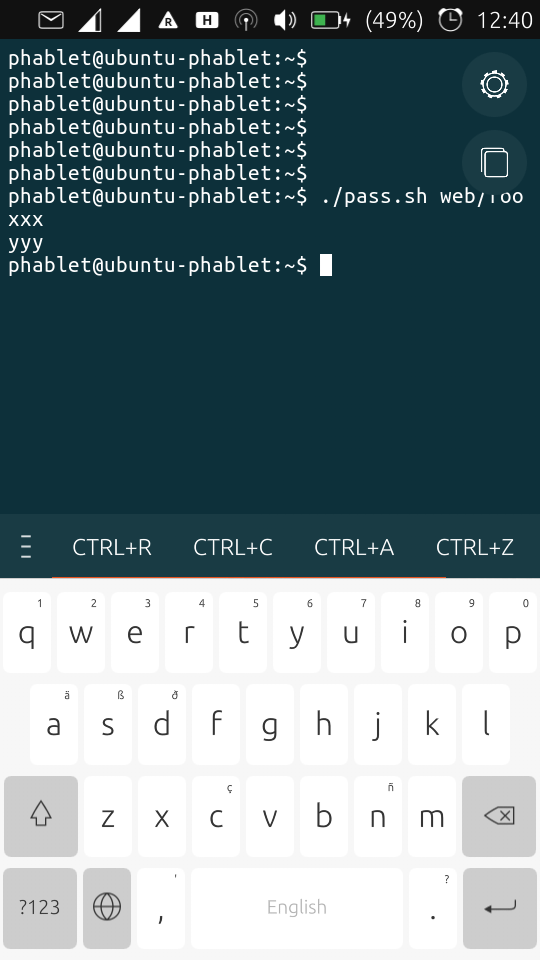
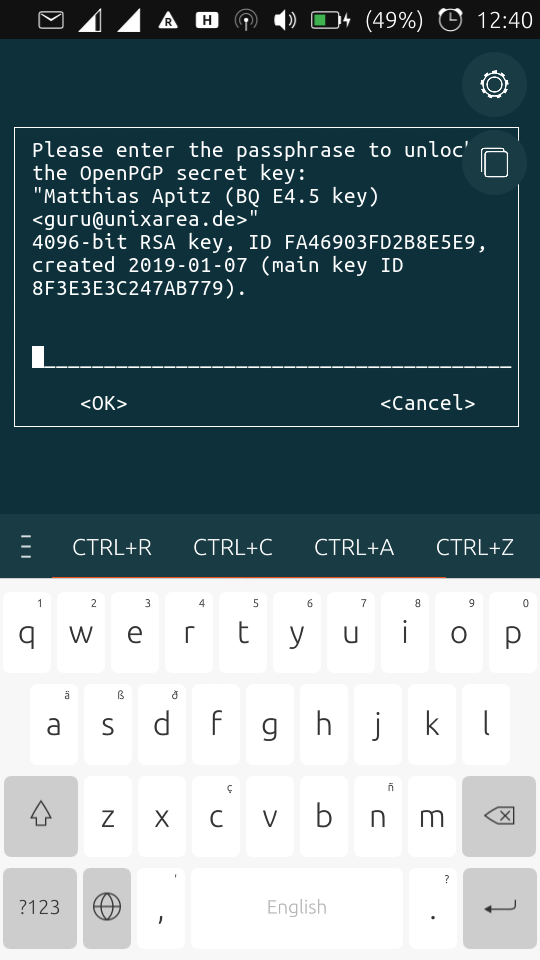
Matthias
-
The problem is: The GnuPG needs a good passphrase, esp. in our case where the device could be lost or teft. Mine is ~8 words long and typing it with the OSK is rather a PITA. Better is using for this an OpenGPG Card, a CCID security USB token. This requires only a 6 digit PIN to unlock the GnuPG keys. It's installation and configuration will be described in part2.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login