uWolf (LibreWolf)
-
Introduction to the uWolf thread.
This thread is dedicated to discussing the uWolf LibreWolf wrapper, where you can ask questions, help with development, and receive updates on the project.
Due to many bugs LANDSCAPE is officially unsupported.
Useful Links
- The uWolf project is hosted on GitHub and can be found here.
- The latest stable release is available on Open Store.

Buy Me A Coffie:
support my ongoing opensource projects, including uWolf here: https://buymeacoffee.com/chromiumos.guy
you have my heartfelt thanks for the donations I received, It means a lot to me and I'm flattered people trust me to this degree.ANNOUNCEMENT:
as you've seen I have not updated this app in while, this is because I'm working on implementing XDG portals in lomiri this will help all xdg apps integrate smoothly Librewolf is an xdg app as well so this project will benefit.
PLANNED (will come with a massive rewrite i am planning the moment my FP5 arrives and i can develop on platform with VSCodium which will enable me to rapidly debug):
- app confinment (@Fuseteam has an MR that needs to be upstreamed first but I will go ahead)
there is already a branch which is compliant and contained, heavily broken though. - fix scaling completely with method @Fuseteam shared
ui_density=0 equals no scaling issues (haven't tested yet so i can't say for sure). - rewrite mobile UI (planning on copying fennec's UI close to 1/1 as possible)
i thought about off-loading UIX changes to an extension but unless i want to do a legacy extension an implementation will take a really long time, so userchrome it is. - Completely rewrite codebase for Noble/Stability (I now know what sticks so I'll write the code with that in mind)
everything will get rewritten in chunks, i will conduct some surveys because i have some ideas that are based on some assumptions that are best confirmed before i act out on said ideas.
Development Log (DEVLOG)
Release: v0.11.38
STATUS: Pending Openstore release
- Added codec support: added libavcodec58. (only works in Noble!)
Release: v0.11.37
STATUS: Released on Github
- Librewolf version update: now
v143.0.3-1
Release: v0.11.36
STATUS: Released on Github
- Librewolf version update: now
v143.0.3-1
Release: v0.11.35
STATUS: Released on Github
- Librewolf version update: now
v143.0.1-1
Release: v0.11.34
STATUS: Released on Openstore
- Librewolf version update: now
v143.0-1 - Icon Change: chanegd icon to the one agreed on below icon made by AdamSchrey
Release: v0.11.32
STATUS: Released on Openstore
- Librewolf version update: now
v142.0-1 - Pathing fix: Pathing is now relative to the
$HOMEvariable instead of a hardcoded username, which will prevent issues if the user's home directory is not/home/username. - Profile Creation Fallback: Fallback is to create a profile if none are found, negating the setup process of previous versions.
Release: v0.10.31
STATUS: Released on Github
- Librewolf version update: now
v141.0.2-1
Release: v0.10.30
STATUS: Released on Openstore
- Generalized path to drm: generalized the path from
/sys/class/drm/card0-DSI-1/modesto/sys/class/drm/*/modesas well as made sure the old virtual framebuffer system is used as fallback, which will fix the crashing problem on specific devices.
Release: v0.10.29
STATUS: Released on GitHub
-
Fixed is_tablet() Function: The function now utilizes the device-info shell command instead of directly reading YAML files. This enhancement improves reliability and bypasses the fact that AppArmor is blocking access to the YAML files and makes the function break.
-
Resolved Profile Change Crash: A significant issue that caused uWolf to crash when writing changes to the profile has been addressed. Although this problem was previously fixed, it required additional confirmation, which is now included in this version to eliminate confusion. The crash was traced back to unusual behavior stemming from the use of both Wayland at the start to obtain screen size with QML and qmlscene before switching to XWayland for the actual application. If this process takes too long, the system loses context and terminates the app. Consequently, if we update the Chrome in the profile, the delay can lead the system to mistakenly believe the app has halted, resulting in a crash.
-
Fallback Scaling Method: The old scaling method, which employed Qt grid units and the environment variable
$GRID_UNIT_PX, is now implemented as a fallback. This adjustment aims to prevent crashes on devices that do not support the getprop handle for DPI, ensuring a smoother user experience even in scenarios where DPI scaling fails.
Release: v0.9.27
STATUS: Released on Openstore
- URL Bar Fix: The URL bar now hides correctly when entering fullscreen mode.
- Tab Bar Fix: Resolved THE issue where the tab bar was interfering with the OSK overlay, by compensating for it. (the one where the overlay overshoots)
- Keyboard Info Gathering Refactor: The method for gathering keyboard information has been completely refactored. The previous reliance on QML has been replaced with a more efficient Python implementation, streamlining the process.
- Scaling Adjustment: Transitioned from grid units (Qt) to DPI-based scaling, providing a consistent experience across different devices.
- Word Ribbon Support Addition: The OSK overlay now supports the word ribbon feature, accommodating the height of the OSK keyboard with or without it.
- OSK Overlay CSS Refactor: The CSS for the OSK overlay has undergone a complete refactoring, finally ensuring good-ish positioning.
- Usage Mode Fix: Corrected the
is_usage_mode_staged()function, which previously defaulted to Staged mode incorrectly.
Release: v0.7.23
STATUS: Released on Openstore
- Librewolf version update: now
v141.0-1
Release: v0.7.21
STATUS: Released on Openstore
- Fixed FP4 Scaling Issues: The scaling issue was resolved by capping the maximum scaling at 2.4 and the minimum at 0.7.
- Fixed Tab Bar Issues in Landscape Mode: The tab bar was rewritten to dynamically adjust margins based on screen percentage instead of using fixed values.
Release: v0.7.18
STATUS: Released on GitHub
- Librewolf version update: now
v140.0.2-1,
note: updating to this version seems to fix addon button killing OSK.
Release: v0.7.17
STATUS: Released on Openstore
- OSK Overlay Improvement: Enhanced OSK overlay height calculations to reduce overshoot, resulting in a more accurate and user-friendly experience.
Release: v0.7.16
STATUS: Released on GitHub
- XUI Improvement: Simplified UI changes have been implemented, significantly enhancing the overall XUI experience. Although settings cannot be accessed while in landscape mode, this change mitigates previous issues. Additionally, addon management is now available, and the bookmark button (star) has been reinstated.
- Location Feature: A location policy has been added, providing uWolf with access to location services.
Release: v0.7.15
STATUS: Released on Openstore
- Search Engine Fix: actual solution implemented as suggested by MrOtherGuy here for the Issue here, no more database Injection.
- Librewolf version update: now
v139.0.4-1
due to little change in overall architecture no flowchart is provided, for up to date flowcharts visit the github repository.
Release: v0.7.14
STATUS: Released on GitHub
- Simplified OSK Hide Mechanism: This release patches osk_config_trigger.uc.js to improve the responsiveness of hiding the OSK overlay while browsing, making it feel less bloated. The change came from shifting focus to the end-user experience and identifying what triggers the OSK to hide.
Release: v0.7.13
STATUS: Released on GitHub
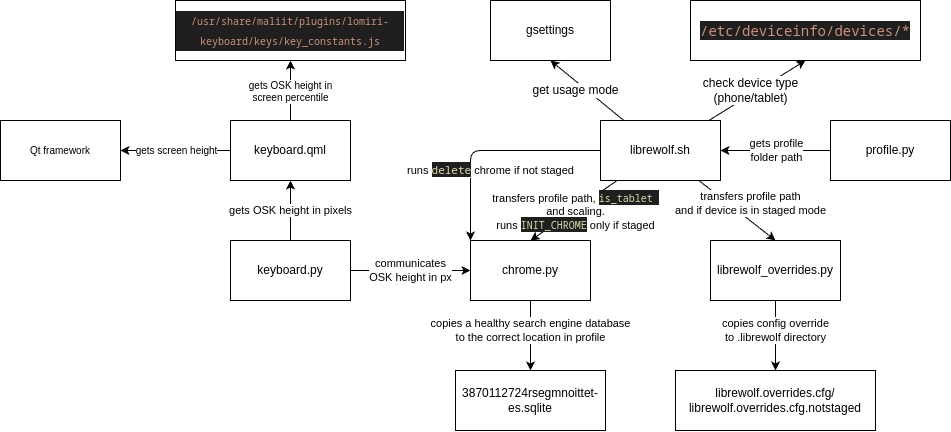
- Search Engine Fix: Alternative Solution: Although the underlying issue persists, I've implemented a workaround by injecting a pre-populated database containing search engine data. This approach circumvents the need for manual configuration, effectively masking the problem. It's essential to note that this is not a bug on my end, but rather a compatibility issue between LibreWolf and fx-autoconfig. I've opened an issue here for those interested in resolving the root cause.
- Enhanced OSK Hide Mechanism: The On-Screen Keyboard (OSK) hide mechanism has been refined to dynamically respond to URL changes. For instance, when searching on a search engine, the OSK overlay will now automatically hide, eliminating the previous awkward behavior that required manual intervention.
For those interested in the technical details of the database injection and to address the security concerns raised by @domubpkm, I've included a flowchart that illustrates the management of the LibreWolf profile. This should provide a clear understanding of the process and help alleviate any concerns.
Release: v0.7.11
STATUS: Released on github
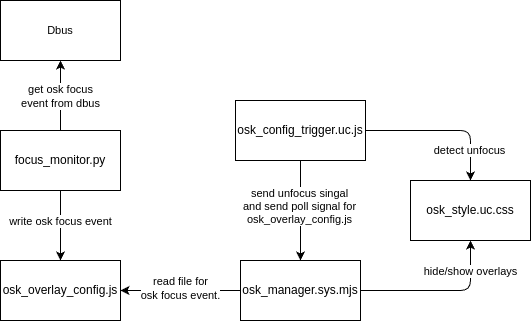
Significant updates have been made in the release:- OSK Dynamic Reactions: The browser detection mechanisms have been replaced with a more robust approach, utilizing a Dbus monitor to listen for OSK focus events. However, this new method has a limitation: the Dbus monitor can only detect when the OSK gains focus, but not when it loses focus. This introduced a challenge in detecting unfocus events, which has been temporarily addressed by implementing a crude solution involving a tinted overlay over the screen. This overlay is active when the OSK overlay is shown, allowing the system to detect when to unfocus.
- Bug Fix: The
is_tabletfunction, which resulted in many crashes in the v0.6.10, has been fixed.
For those interested in a more detailed understanding of the new OSK dynamic reactions architecture, a flow chart is provided.
If you have any questions or would like to discuss the development of uWolf, please don't hesitate to ask in this thread. Your input and feedback are valuable to the project. Feel free to share your thoughts, suggestions, or concerns, and I'll do my best to address them.
-
C ChromiumOS-Guy referenced this topic on
-
First, a big thank you for the development of this new browser. There is such a lack of a functional browser that we cannot even go to Github currently.
I must admit that I have not yet tried on my daily phone Volla 22, waiting for the at least a beta or stable version in the OpenStore. But thank you for the future.
Only one question for the moment : is the browser secure ? No particular security risk that you have noticed ?
-
@domubpkm There is a security issue, but it's relatively minor and manageable. The problem lies in JavaScript files with privileged execution that can access browser internals and read files on the host. However, the risk is mitigated by the fact that:
- Librewolf stores sessions in cache, so malicious code would only execute in the next session (after restart)
- The sensitive files are re-read and replaced every time a session is launched, making it difficult for changes to persist
- The time window for tampering with the files is small (between verification of the Chrome folder and Librewolf launch)
To further reduce the risk, encryption and obfuscation of the sensitive files could be implemented, but this would make it harder for me (the developer) to test and debug code. The issue will be addressed once the more significant problems are resolved.
It's worth noting that Librewolf is considered a secure browser, and the privileged code execution is heavily sandboxed, preventing access to web content among other things. While this issue could potentially be exploited to steal data, the overall security of the browser is still robust, and any other security problems would likely originate from the Librewolf/Firefox source code itself.
-
@ChromiumOS-Guy Thank you for your clear explanations. I imagine that in time, you will do everything to make this browser as sure as possible. In any case, your initiative is praised by all.
-
Hello.
For everyone use :You have specified the installation process. Can you specify the GitHub's uninstallation process: I would like to know if everything that was brought during the installation is well uninstalled in UT Tweak Tools use (Clearing Cache, Config, Data and Desinstalling App). Or if there are other things to do.
Can you specify again what you have to do when going from one .Click to the other.
Thanks in advance
-
@domubpkm I have tried a few of the versions now and have updated both through the OpenStore in the usual way and using UTTT to remove all the items you list and later download from and remove GitHub versions as you would with any other app. All with no problem.
-
-
@ChromiumOS-Guy Hello.
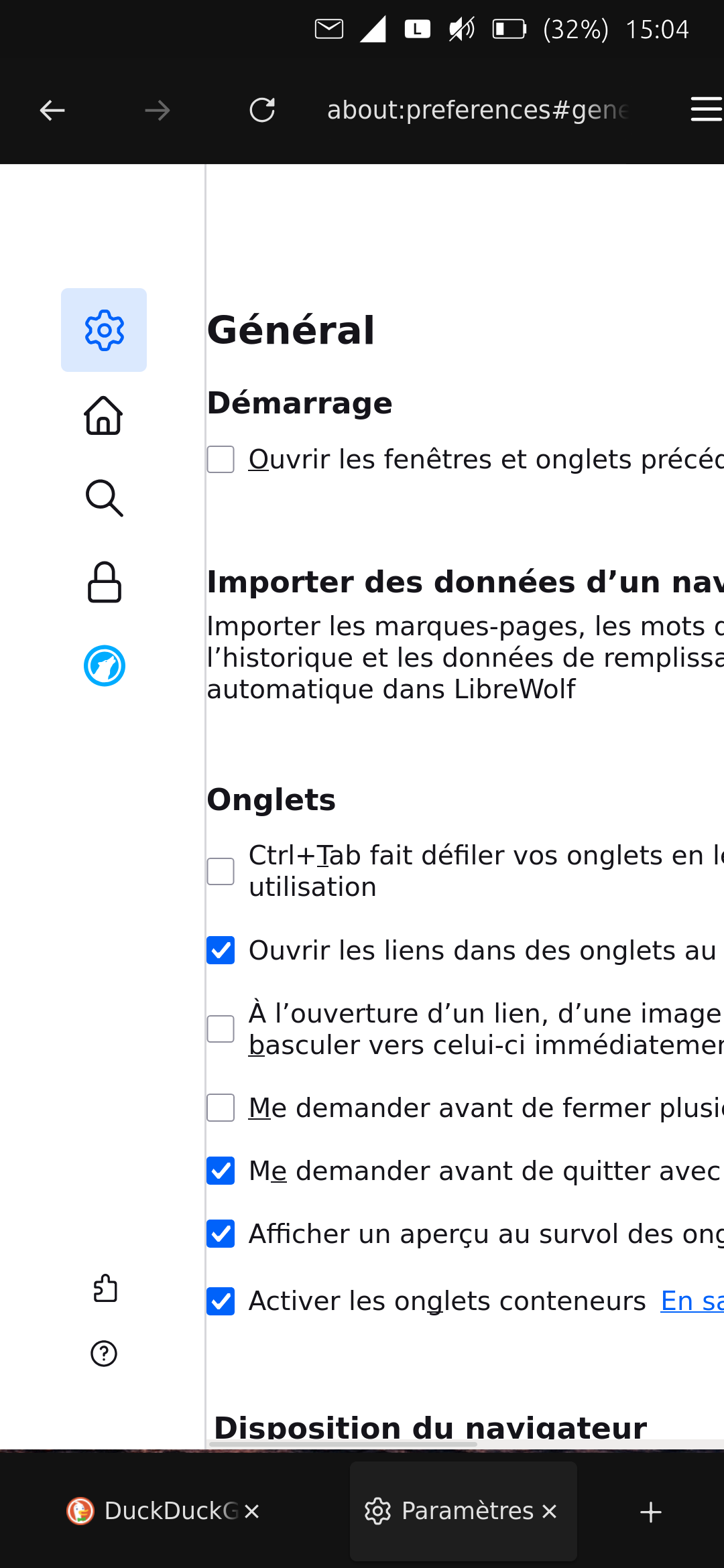
First tests V O.7.15 (OpenStore) on Volla 22 Focal OTA-9 :
-
First the browser starts normally and does not crash, which is already very promising!
-
The keyboard does not always go up, especially noticed when I switch from one tab to another.
-
The drop-down menus are not always unfolding.
-
Copy / paste is non-functional and it lacks.
-
I do not see an icon uBlock Origin which allows access to actions on web pages, for example blocking certain elements.
The parameter subdivisions mark is too wide on the Volla 22.
Overall, I have a very positive impression for such a young version.
 So well done, nice work !
So well done, nice work ! -
-
Amazing work so far. Though a few critical UX bugs still cause a lot of pain:
- When rotating the phone into landscape mode, inputs on the right side of the screen don't work.
- In portrait mode, the main menu is not shown (and because of 1. you can't open it in landscape mode. You can get there through the extensions -> manage extensions -> settings gears for now.
- Dropdown menus, mostly the ones in the settings, often don't work, such as the one to select what is shown on new windows/tabs. But sometimes they do. You tap the menu and it gives some visual feedback of being activated, but nothing happens.
- Sometimes on new tabs the on screen keyboard doesn't work at all. I think it starts working after long pressing something that opens a menu.
- Once you have 3 tabs open in landscape mode, there is no button to create a new tab. Though you can long press a tab and then choose "New Tab to Right". edit: The button might just be cropped off for me because of 7?
- Input completion particularly in the url bar is still broken. E.g. the readme suggests clearing the startup cache in about:support. But as soon as I type the : after
about:, it "corrects" it toabtut:. When I press backspace then, it "corrects" toabtutabtut. With a combination of long pressing backspace and selecting the non-corrected word at the top of the keyboard you can get there but it's quite painful. - Content is slightly cropped on the right side on Volla Quintus ("algiz"). $GRID_UNIT_PX is 21
- In the previous version, attempting location access would flicker the in-browser permission dialog and crash (OOM?) the phone after a few seconds. Now the in-browser permission dialog works but I seem to be stuck in Hamburg and there is no OS permission request, also no uWolf in the App Permissions -> Location. Will this need completely new code in uWolf, or can the default desktop linux location support be reused? Similarly (I guess) I first tried to authenticate with my Solo USB-C key with bitwarden but it didn't actually do the USB request I guess - I don't think this is going to be a high priority, just wanted to note it.

- Startup "Open previous windows and tabs" setting doesn't work, and history always seems to be empty when enabled on the new tab page. Probably related to the no search engines thing? But iirc it did work in the last openstore version.
Do you want to take donations? Or are you already paid for this work? Because this might be one of the most important things happening right now for Ubuntu Touch, so thank you either way!
-
Do note that some of these issues are due to integration of the desktop browser into UT, not necessarily something that can be solved in the packaging.
Some of these bugs will have to be taken up with upstream (e.g. menu and tabs going offscreen and setting pages not fitting the screen), others will have to solved in UT (e.g. right side being unusable in landscape)
Some are being looked into e.g. right side being usable will afaict be fixed by https://gitlab.com/ubports/development/core/lomiri/-/merge_requests/207 and the settings page not fitting might be improve the new design lands: https://connect.mozilla.org/t5/discussions/firefox-settings-design-share-your-input/m-p/66629/highlight/true#M23625
While i am sure that donations are appreciated, do keep in mind this won't brings fixes faster as there is only so much we can do.
Have ideas how firefox (and by extension librewolf) can be improved for us? share ideas to upstream, but be nice and be mindful these things takes time* to fix and may not be their current priority. Showing genuine interest, doing research if something has been proposed before and sharing ideas so they may gain traction is highly appreciated
* to help shape perspective It took 3 years (compare the date on https://connect.mozilla.org/t5/discussions/arm64-armhf-firefox-binary-tarballs-for-packaging-for-ubuntu/m-p/12847 with https://www.mozilla.org/en-US/firefox/136.0/releasenotes/) for them to finally package for arm64 in their own apt repo, in part because it took that long of sharing for it take traction but also in part due to changes they had to made
-
@haagch and @domubpkm here are the bugs you reported and what I can do about them:
-
Keyboard does not always appear, especially when switching between tabs (OSK design, I have no control over)
-
Drop-down menus do not always unfold ("define" drop-down settings and subsidiary menus inside it work)
-
Copy/paste functionality is non-functional (in Known Issues already, please read them.)
-
uBlock Origin icon is not visible, making it difficult to access actions on web pages (thats intentional design out of compromise, I will modify UI much more aggressively instead of hiding UI elements)
-
Parameter subdivisions mark is too wide on the Volla 22 (read my message about scaling Issues)
-
Inputs on the right side of the screen do not work in landscape mode (xwayland will probably fix itself when the move to wayland is done, added to Known Issues)
-
Main menu is not shown in portrait mode ("define: main menu, the settings button?, if so this is a scaling issue).
-
Dropdown menus in settings often do not work (please elaborate further, open an Issues and github and provide me with screenshots and logs please.)
-
On-screen keyboard does not work on new tabs, but starts working after long pressing something that opens a menu (known behavior, 10. very hard to pin down, but essentially boils down to "wait a bit: as it seems OSK plugin initializes last.)
-
No button to create a new tab when 3 tabs are open in landscape mode (is this related to reported bug 6, or something else like scaling elaborate).
-
Input completion is broken, especially in the URL bar (elaborate, Is not broken this is specific to you and you may also misunderstood the problem, if you have severe scaling issues the url bar will go off screen and "Expand" to the new "space" if that happens you won't see suggestions).
-
Content is slightly cropped on the right side on Volla Quintus (again scaling)
-
Location access does not work, and there is no OS permission request (I can give it access, and you'll have to test if it works as my phone does not have good GPS capabilities and is incapable of first fix)
-
Startup "Open previous windows and tabs" setting does not work, and history is always empty when enabled on the new tab page
-
Authentication with Solo USB-C key with bitwarden does not work (all of these work for me except bitwarden I don't use it, and I doubt it would work through UT, you can open an Issue that uWolf cannot detect USB-C auth keys)
-
-
also I say scaling Issues, but let me elaborate, firefox/librewolf UI is shit and does not handle being squeezed so much they did not code it correctly so it breaks (usually by overflowing of screen), i already have many many counter-measures ainly in the form of sacrificial UIX elements like addon buttons being tampered with so the urlbar prioritizes overflowing onto them first, among many many padding rules.
I have decided this is not enough (insert Thanos scene).
go to here, help if you can.about donations I much rather you'd give me you're time in the form of help, help in anyway possible.
I won't go into too much detail about my life but I cannot guarantee I can maintain this project for years like my past projects, I may fine uni really easy or get a post in the army that lets me have a lot of free time, or I may not so I cannot and will not take donations for something I cannot guarantee, due to my drafting date coming up in 2026 either I go to uni then to the army or directly to it. -
@ChromiumOS-Guy Hello thanks for your explanations.
One more thing i noticed : is it possible to save bookmarks currently ? -
@domubpkm its LibreWolf, it should work just as well, the bookmark bar is hidden so you will have to access through settings -> bookmarks
the button to bookmark is probably also hidden so you will need to manually enter a bookmark.
-
@ChromiumOS-Guy Yes i hadn't seen a bookmark button so as to record , but i wanted to be be sure that i hadn't miss something.
-
@domubpkm I'm currently going to do a massive rewrite of UI, this will fully adopt UI to mobile by extensive use of javascript this will also be unstable and take at least a week to do and another to get stable.
-
-
@Fuseteam With main menu I mean the hamburger menu with the three lines.
Made some videos for some of the things.
1: Solo USB key, it's supposed to turn blue when an auth request comes to it. Idk if it needs some kind of usb permission: https://youtube.com/shorts/EIjAkhwfOOw
2. Drop down boxes in the settings page, I think this might be related to the on screen keyboard because it starts working after a menu opens: https://youtube.com/shorts/o5OpgXKtTWk
3. Broken auto complete in the url bar: This time it seems to have learned not to auto correct "about:", but backspace still autocompletes quite broken stuff: https://youtube.com/shorts/Uc5UlPfpEXg -
@haagch couldn't help but notice this is on first boot without my custom chrome.
also suggestions work perfectly what you're seeing is the hard work of Maliit auto-complete its annoying as hell and you can turn it off in the settings this is not related to my app.
-
@ChromiumOS-Guy I had first installed the old 0.4 stable version from open store, then I tried the click package from the github releases and noticed it didn't read my existing profile. I also downgraded to the open store version again, then installed the latest upgrade from openstore. I guess this was not a good thing to do.
I now uninstalled the app from openstore, deleted ~/.librefox and installed it again. The auto install script ran again and I now have the tabs at the bottom again. Your modifications solve my issue 2.: The main menu hamburger button is now visible and clickable in portrait mode. It also solves 5, a new tab button is always visible now. So disregard these, as these were my own fault I guess.
What I can't seem to find in your modification is a way to access extensions. In portrait mode I see none, in landscape mode I see (unclickable because of 1.) icons for ublock, privacy badger and sponsor block but no overflow for further extensions, in particular I can't see a way to access the bitwarden extension at all. If you could manage to squeeze the extensions container (the puzzle tile) icon somewhere in this UI that would help a lot I think.
"Word suggestions" seems to be the name for auto complete, I disabled that for now, thanks. I know just a little bit about input/completion with virtual keyboards and I guess in x11/xwayland it'll always be a bit broken (I'd think currently it just fails to send an appropriate amount of backspaces before sending the "completed & corrected" word). But even on wayland the protocols aren't great. I remember being in the audience of this fosdem talk: https://archive.fosdem.org/2024/schedule/event/fosdem-2024-2972-wayland-s-input-method-is-broken-and-it-s-my-fault/