Trying to revive 'ubtd' (Bluetooth file transfer)
-
OK, yet more updates.
As already indicated above, my app now successfully registers with D-Bus/OBEX:
[20/01/2026 13:50] Creating a QMirClientScreen now [20/01/2026 13:50] reply QDBusMessage(type=MethodReturn, service=":1.28", signature="", contents=([]) ) [20/01/2026 13:50] creating agent on dbus [20/01/2026 13:50] registering agent [20/01/2026 13:50] discovering obex service [20/01/2026 13:50] OBEX service not found, attempting D-Bus activation [20/01/2026 13:50] OBEX service activated successfully [20/01/2026 13:50] found OBEX service at: "org.bluez.obex" [20/01/2026 13:50] registering agent on obexd-server [20/01/2026 13:50] Agent registered successfully [20/01/2026 13:50] have entries: (".", "..", "HubIncoming", "qmlcache", "qtshadercache-arm64-little_endian-lp64") "/home/phablet/.cache/ratatoskr.philipa" [20/01/2026 13:50] file:///usr/lib/aarch64-linux-gnu/qt5/qml/Lomiri/Components/1.3/Icon.qml:115:5: QML Image: Failed to get image from provider: image://theme/network-cellular-connected [20/01/2026 13:50] QObject::startTimer: Timers cannot be started from another thread [20/01/2026 13:52] file:///usr/lib/aarch64-linux-gnu/qt5/qml/Lomiri/Components/1.3/Icon.qml:115:5: QML Image: Failed to get image from provider: image://theme/network-cellular-connected [20/01/2026 13:52] file:///usr/lib/aarch64-linux-gnu/qt5/qml/Lomiri/Components/1.3/Icon.qml:115:5: QML Image: Failed to get image from provider: image://theme/network-cellular-connected [20/01/2026 13:52] qt.qpa.mirclient: Attempted to deliver an event to a non-existent window, ignoring.But when I start the app and try to push a file from the laptop to the phone over BT,
obexdlogs the following:[20/01/2026 13:50] OBEX daemon 5.64 [20/01/2026 13:50] Excluding pcsuite [20/01/2026 13:50] Excluding ftp [20/01/2026 13:50] Excluding irmc [20/01/2026 13:50] Excluding mas [20/01/2026 13:51] CONNECT(0x0), <unknown>(0xff) [20/01/2026 13:51] CONNECT(0x0), <unknown>(0x0) [20/01/2026 13:51] PUT(0x2), <unknown>(0xff) [20/01/2026 13:51] Agent replied with an error: org.freedesktop.DBus.Error.AccessDenied, An AppArmor policy prevents this sender from sending this message to this recipient; type="method_call", sender=":1.107" (uid=32011 pid=4463 comm="/usr/lib/bluetooth/obexd -P ftp,irmc,mas,pcsuite -" label="unconfined") interface="org.bluez.obex.Agent1" member="AuthorizePush" error name="(unset)" requested_reply="0" destination=":1.106" (uid=32011 pid=4460 comm="ratatoskr " label="ratatoskr.philipa_ratatoskr_260120124119 (enforce)") [20/01/2026 13:51] PUT(0x2), Forbidden(0x43) [20/01/2026 13:51] DISCONNECT(0x1), <unknown>(0xff) [20/01/2026 13:51] DISCONNECT(0x1), Success(0x20) [20/01/2026 13:51] disconnected: Transport got disconnectedLooking in journal, another message is found right before the error reported by
obexd, this one issued bydbus-daemon(here copied from an earlier test run):Jan 15 16:44:14 hatshepsut dbus-daemon[2372]: apparmor="DENIED" operation="dbus_method_call" bus="session" path="/test/agent" interface="org.bluez.obex.Agent1" member="AuthorizePush" name=":1.94" mask="receive" pid=5216 label="ratatoskr.philipa_ratatoskr_260115153557" peer_pid=3539 peer_label="unconfined"Clearly, the IPC between
obexdand the agent registered by my app seems to be blocked by AppArmor. This is the current AA profile for my app:{ "policy_groups": [ "bluetooth", "networking", "content_exchange", "content_exchange_source" ], "policy_version": 20.04 }Can anyone tell me what could be missing?
-
@PhAndersson said in Trying to revive 'ubtd' (Bluetooth file transfer):
AuthorizePush
this is denied; I never dabbled much with Apparmor, and certainly not with UT; I notice with some dismay that there are no apparmor logs and I have no clear idea on the better way to enable them unfortunately.
For now, I have only one positive thing to say: in the application that worked with 16.04, the template was set to 'unconfined'; while this is not generally a great idea, to advance your testing maybe it could be worth a try to add it to the apparmor profile ?
-
@gpatel-fr said in Trying to revive 'ubtd' (Bluetooth file transfer):
For now, I have only one positive thing to say: in the application that worked with 16.04, the template was set to 'unconfined'; while this is not generally a great idea, to advance your testing maybe it could be worth a try to add it to the apparmor profile ?
Yes, you're right -- it's certainly worth a try.
-
Well, good news! With the "unconfined" AA profile, the app works

The phone successfully received a
.jpegfile sent over BT from my laptop: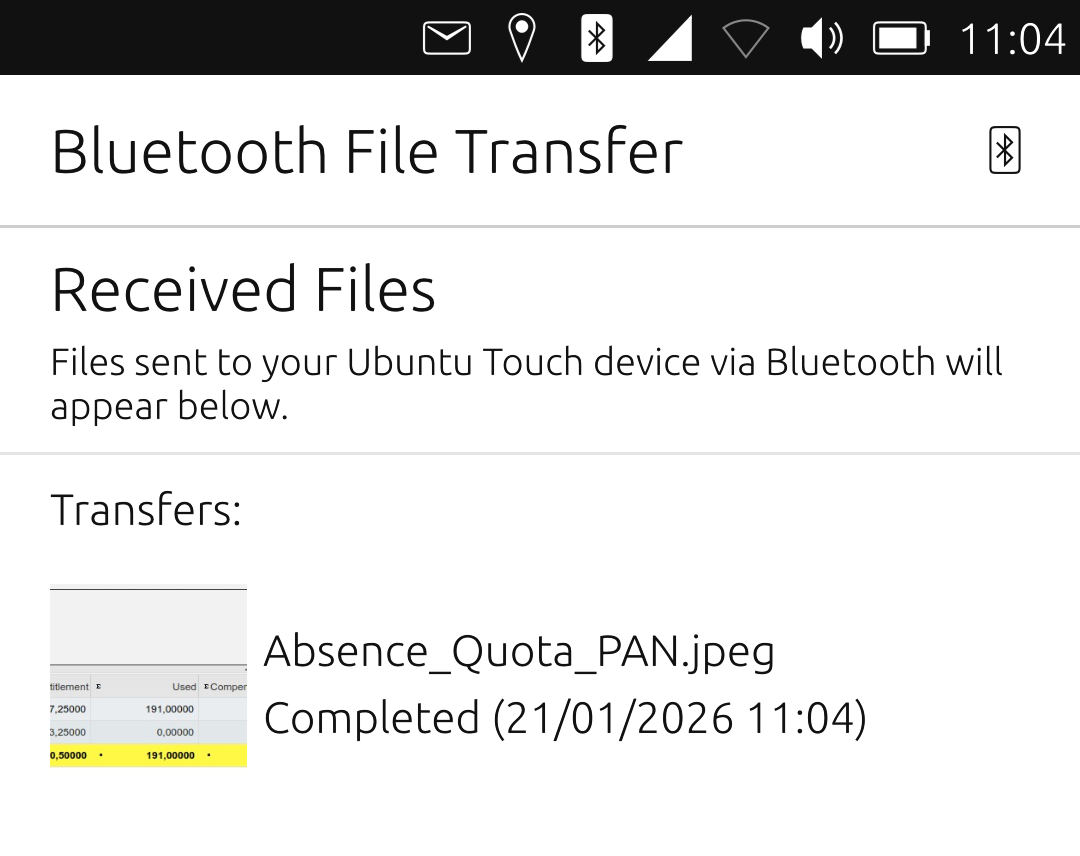
-
Great ! have happy file exchanges with your car

-
@PhAndersson said in Trying to revive 'ubtd' (Bluetooth file transfer):
Well, good news! With the "unconfined" AA profile, the app works

The phone successfully received a
.jpegfile sent over BT from my laptop:
Congrats, So some changes are needed on UT to make it work ?
-
@gpatel-fr said in Trying to revive 'ubtd' (Bluetooth file transfer):
Great ! have happy file exchanges with your car

That won't work yet, unfortunately. For this, I need the SharePlugin to work. That one still crashes as soon as I select it which causes the phone to restart.
More troubleshooting needed

-
@lduboeuf said in Trying to revive 'ubtd' (Bluetooth file transfer):
Congrats, So some changes are needed on UT to make it work ?
If your question is: did I need to hack my phone to make the app work in its current state, then the answer is no. As suggested by @gpatel-fr, I just gave it an "unconfined" AA profile (which I understand would prevent me from publishing it on the OpenStore).
So eventually an updated
bluetoothAppArmor Policy Group would be needed, I guess (or a extra one dedicated to OBEX). -
@PhAndersson I think any spawning of external processes that are not inside the app's
~/.local/sharedirectory require unconfined. And in this case, unconfined would be required since it's using some system executable. -
@projectmoon said in Trying to revive 'ubtd' (Bluetooth file transfer):
I think any spawning of external processes that are not inside the app's ~/.local/share directory require unconfined.
If 'running an external process' means 'activating a service' via dbusk, not 'spawning', it can be done from confined I think. I did not check how exactly is working this application.
-
@PhAndersson said in Trying to revive 'ubtd' (Bluetooth file transfer):
prevent me from publishing it on the OpenStore
Not sure of that actually, there are applications with a big red scary warning, that do not prevent them to be published.
Also, IIRC the idea on phone OS is that the app is shipped with granular authorizations policy and the user grant these rights or not. I don't see why you could not ship a granular apparmor policy for the app if you wanted to do so.
-
@gpatel-fr said in Trying to revive 'ubtd' (Bluetooth file transfer):
@PhAndersson said in Trying to revive 'ubtd' (Bluetooth file transfer):
prevent me from publishing it on the OpenStore
Not sure of that actually, there are applications with a big red scary warning, that do not prevent them to be published.
Also, IIRC the idea on phone OS is that the app is shipped with granular authorizations policy and the user grant these rights or not. I don't see why you could not ship a granular apparmor policy for the app if you wanted to do so.
For such application to be exposed to the Openstore one will have to ask the Openstore team for validation/ review
-
@gpatel-fr said in Trying to revive 'ubtd' (Bluetooth file transfer):
@projectmoon said in Trying to revive 'ubtd' (Bluetooth file transfer):
I think any spawning of external processes that are not inside the app's ~/.local/share directory require unconfined.
If 'running an external process' means 'activating a service' via dbusk, not 'spawning', it can be done from confined I think. I did not check how exactly is working this application.
Yes, that was my experience as well. Even with an enforcing AA profile, my app was able to ask D-Bus to start the OBEX daemon if needed.
Only certain types of D-Bus requested are blocked by AA (such as
AuthorizePush-- see log extract in one of my posts above). -
@PhAndersson said in Trying to revive 'ubtd' (Bluetooth file transfer):
certain types of D-Bus requested are blocked by AA (such as AuthorizePush
I have actually taken a look at the ubtd code and as I understand it AuthorizePush is a method defined by ubtd for obex.
Looking at the Ubuntu touch bluez code with some dismay, it seems that this method is defined quite officially to allow the obex daemon to send data to a client, squarely fitting your use case, so why is there no apparmor policy for that ? As a wild guess, it looks like an oversight by Canonical that was forwarded by Ubuntu Touch - or even an oversight by Debian, forwarded by Canonical, forwarded by Ubuntu Touch. Maybe a bluetooth policy should exist.
Or maybe it already exists ? looking at usr.sbin.cupsd in my Kubuntu 24.04 installation, I see a string 'network bluetooth'. Maybe adding that to your apparmor profile could strike gold ? Absolutely wild guess of course

-
@gpatel-fr said in Trying to revive 'ubtd' (Bluetooth file transfer):
@PhAndersson said in Trying to revive 'ubtd' (Bluetooth file transfer):
certain types of D-Bus requested are blocked by AA (such as AuthorizePush
I have actually taken a look at the ubtd code and as I understand it AuthorizePush is a method defined by ubtd for obex.
Correct -- it's still present in my current code.
Looking at the Ubuntu touch bluez code with some dismay, it seems that this method is defined quite officially to allow the obex daemon to send data to a client, squarely fitting your use case, so why is there no apparmor policy for that ? As a wild guess, it looks like an oversight by Canonical that was forwarded by Ubuntu Touch - or even an oversight by Debian, forwarded by Canonical, forwarded by Ubuntu Touch. Maybe a bluetooth policy should exist.
Well, there is a
bluetoothpolicy group, and I used it. But it doesn't seem to cover that use case.Or maybe it already exists ? looking at usr.sbin.cupsd in my Kubuntu 24.04 installation, I see a string 'network bluetooth'. Maybe adding that to your apparmor profile could strike gold ? Absolutely wild guess of course

If you refer to the
networkandbluetoothpolicy groups, I already use both (as you will see in one of my earlier posts), but that was not enough.If there is a way to extend an app AA profile past the predefined policy groups offered by the platform, I would be interested. Can you point me to a doc. that covers it? I already tried hacking the
.apparmorfile provided with my app, butclickabledidn't seem to approve
-
My knowledge of apparmor is basic unfortunately. In particular, interaction with dbus is something I never looked at before UT, and bluetooth and network management with apparmor is totally unknown to me.
Yes my suggestion of using network bluetooth was not very well thought out, I was believing that maybe there was special in associating the two, as if there was a right called network_bluetooth. My bad

This said, there is something that bothers me in your log: it suggest that there is a denial in the sending FROM the server (the systemd service) TO your app. Usually when a sending is denied, it is the sender that is lacking rights.
So following this idea, it could be the system itself that is missing a configuration. However, see above, I have no idea how rights are managed for the bluetooth services.
Maybe all that is needed is to add an apparmor profile for the obexd executable, but often the obvious solution is wrong.
Note that if you want to test it, there is no need to turn your rootfs r/w, with overlay or bind-root you can 'add' stuff in read only directories.Sorry not to be more specific, but going deep in system administration takes time and concentration and I'm currently in other stuff.
-
Right, while searching for another problem, I just stumbled on something that looks like an answer.
there is in this directory:
/etc/dbus-1/system.d
a bunch of files configuring the authorizations for dbus; for example (taken for its brevity):cat com.lomiri.UserMetrics.conf <!DOCTYPE busconfig PUBLIC "-//freedesktop//DTD D-BUS Bus Configuration 1.0//EN" "http://www.freedesktop.org/standards/dbus/1.0/busconfig.dtd"> <busconfig> <policy user="usermetrics"> <allow own="com.lomiri.UserMetrics"/> </policy> <policy context="default"> <allow send_destination="com.lomiri.UserMetrics"/> <allow receive_sender="com.lomiri.UserMetrics"/> </policy>Now, it's sure that the system.d directory does not seem the right place for a user level service.
At the moment I have no clue where a file configuring the dbus authorization for the org.bluez.obexd service should be created.
But I tend to think that creating one is the proper thing to do because I don't see a reason why obexd should be forbidden to send message to its agents. It should be allowed whatever security reason there is to block general message sending. So this could be the proper way (TM) for your application to run confined. -
Another quick update.
I'm really pleased to announce that I got the SharePlugin part of the app working as well. I successfully pushed a file from my Pixel 3a to my (Linux) laptop over BT, but even more importantly for me, I was able to push selected contacts to my car kit

The user interface is still too rough for the app to be published as is (at this stage, you have to select the target device based on its MAC address, which is far from convenient), but I'm working on it.
-
how about setting up a public directory of what you have (if you have cleared the license question) ? It'll allow me to test it under Noble and possibly send a MR to gitlab once I'm sure that it works. Don't want to harass you of course, it's up to you to decide.
-
@gpatel-fr said in Trying to revive 'ubtd' (Bluetooth file transfer):
how about setting up a public directory of what you have (if you have cleared the license question) ? It'll allow me to test it under Noble and possibly send a MR to gitlab once I'm sure that it works. Don't want to harass you of course, it's up to you to decide.
Yes, the licensing issue has been cleared up. Michael Zanetti agreed with me using the GPL v3.
What I'm working on right now is getting the code in a state where I could submit it on the OpenStore (with the understanding that it would need a full review as it still uses an unconfined profile). Of course, in the process, I will also push the code to a public Github repository.
Can you clarify what the Gitlab merge request you mentioned would be about? I'm afraid I missed a step here.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login