Introduction to the uWolf thread.
This thread is dedicated to discussing the uWolf LibreWolf wrapper, where you can ask questions, help with development, and receive updates on the project.
Due to many bugs LANDSCAPE is officially unsupported.
Useful Links
- The uWolf project is hosted on GitHub and can be found here.
- The latest stable release is available on Open Store.

Buy Me A Coffie:
support my ongoing opensource projects, including uWolf here: https://buymeacoffee.com/chromiumos.guy
you have my heartfelt thanks for the donations I received, It means a lot to me and I'm flattered people trust me to this degree.
ANNOUNCEMENT:
as you've seen I have not updated this app in while, this is because I'm working on implementing XDG portals in lomiri this will help all xdg apps integrate smoothly Librewolf is an xdg app as well so this project will benefit.
PLANNED (will come with a massive rewrite i am planning the moment my FP5 arrives and i can develop on platform with VSCodium which will enable me to rapidly debug):
- app confinment (@Fuseteam has an MR that needs to be upstreamed first but I will go ahead)
there is already a branch which is compliant and contained, heavily broken though. - fix scaling completely with method @Fuseteam shared
ui_density=0 equals no scaling issues (haven't tested yet so i can't say for sure). - rewrite mobile UI (planning on copying fennec's UI close to 1/1 as possible)
i thought about off-loading UIX changes to an extension but unless i want to do a legacy extension an implementation will take a really long time, so userchrome it is. - Completely rewrite codebase for Noble/Stability (I now know what sticks so I'll write the code with that in mind)
everything will get rewritten in chunks, i will conduct some surveys because i have some ideas that are based on some assumptions that are best confirmed before i act out on said ideas.
Development Log (DEVLOG)
Release: v0.11.38
STATUS: Pending Openstore release
- Added codec support: added libavcodec58. (only works in Noble!)
Release: v0.11.37
STATUS: Released on Github
- Librewolf version update: now
v143.0.3-1
Release: v0.11.36
STATUS: Released on Github
- Librewolf version update: now
v143.0.3-1
Release: v0.11.35
STATUS: Released on Github
- Librewolf version update: now
v143.0.1-1
Release: v0.11.34
STATUS: Released on Openstore
- Librewolf version update: now
v143.0-1 - Icon Change: chanegd icon to the one agreed on below icon made by AdamSchrey
Release: v0.11.32
STATUS: Released on Openstore
- Librewolf version update: now
v142.0-1 - Pathing fix: Pathing is now relative to the
$HOMEvariable instead of a hardcoded username, which will prevent issues if the user's home directory is not/home/username. - Profile Creation Fallback: Fallback is to create a profile if none are found, negating the setup process of previous versions.
Release: v0.10.31
STATUS: Released on Github
- Librewolf version update: now
v141.0.2-1
Release: v0.10.30
STATUS: Released on Openstore
- Generalized path to drm: generalized the path from
/sys/class/drm/card0-DSI-1/modesto/sys/class/drm/*/modesas well as made sure the old virtual framebuffer system is used as fallback, which will fix the crashing problem on specific devices.
Release: v0.10.29
STATUS: Released on GitHub
-
Fixed is_tablet() Function: The function now utilizes the device-info shell command instead of directly reading YAML files. This enhancement improves reliability and bypasses the fact that AppArmor is blocking access to the YAML files and makes the function break.
-
Resolved Profile Change Crash: A significant issue that caused uWolf to crash when writing changes to the profile has been addressed. Although this problem was previously fixed, it required additional confirmation, which is now included in this version to eliminate confusion. The crash was traced back to unusual behavior stemming from the use of both Wayland at the start to obtain screen size with QML and qmlscene before switching to XWayland for the actual application. If this process takes too long, the system loses context and terminates the app. Consequently, if we update the Chrome in the profile, the delay can lead the system to mistakenly believe the app has halted, resulting in a crash.
-
Fallback Scaling Method: The old scaling method, which employed Qt grid units and the environment variable
$GRID_UNIT_PX, is now implemented as a fallback. This adjustment aims to prevent crashes on devices that do not support the getprop handle for DPI, ensuring a smoother user experience even in scenarios where DPI scaling fails.
Release: v0.9.27
STATUS: Released on Openstore
- URL Bar Fix: The URL bar now hides correctly when entering fullscreen mode.
- Tab Bar Fix: Resolved THE issue where the tab bar was interfering with the OSK overlay, by compensating for it. (the one where the overlay overshoots)
- Keyboard Info Gathering Refactor: The method for gathering keyboard information has been completely refactored. The previous reliance on QML has been replaced with a more efficient Python implementation, streamlining the process.
- Scaling Adjustment: Transitioned from grid units (Qt) to DPI-based scaling, providing a consistent experience across different devices.
- Word Ribbon Support Addition: The OSK overlay now supports the word ribbon feature, accommodating the height of the OSK keyboard with or without it.
- OSK Overlay CSS Refactor: The CSS for the OSK overlay has undergone a complete refactoring, finally ensuring good-ish positioning.
- Usage Mode Fix: Corrected the
is_usage_mode_staged()function, which previously defaulted to Staged mode incorrectly.
Release: v0.7.23
STATUS: Released on Openstore
- Librewolf version update: now
v141.0-1
Release: v0.7.21
STATUS: Released on Openstore
- Fixed FP4 Scaling Issues: The scaling issue was resolved by capping the maximum scaling at 2.4 and the minimum at 0.7.
- Fixed Tab Bar Issues in Landscape Mode: The tab bar was rewritten to dynamically adjust margins based on screen percentage instead of using fixed values.
Release: v0.7.18
STATUS: Released on GitHub
- Librewolf version update: now
v140.0.2-1,
note: updating to this version seems to fix addon button killing OSK.
Release: v0.7.17
STATUS: Released on Openstore
- OSK Overlay Improvement: Enhanced OSK overlay height calculations to reduce overshoot, resulting in a more accurate and user-friendly experience.
Release: v0.7.16
STATUS: Released on GitHub
- XUI Improvement: Simplified UI changes have been implemented, significantly enhancing the overall XUI experience. Although settings cannot be accessed while in landscape mode, this change mitigates previous issues. Additionally, addon management is now available, and the bookmark button (star) has been reinstated.
- Location Feature: A location policy has been added, providing uWolf with access to location services.
Release: v0.7.15
STATUS: Released on Openstore
- Search Engine Fix: actual solution implemented as suggested by MrOtherGuy here for the Issue here, no more database Injection.
- Librewolf version update: now
v139.0.4-1
due to little change in overall architecture no flowchart is provided, for up to date flowcharts visit the github repository.
Release: v0.7.14
STATUS: Released on GitHub
- Simplified OSK Hide Mechanism: This release patches osk_config_trigger.uc.js to improve the responsiveness of hiding the OSK overlay while browsing, making it feel less bloated. The change came from shifting focus to the end-user experience and identifying what triggers the OSK to hide.
Release: v0.7.13
STATUS: Released on GitHub
- Search Engine Fix: Alternative Solution: Although the underlying issue persists, I've implemented a workaround by injecting a pre-populated database containing search engine data. This approach circumvents the need for manual configuration, effectively masking the problem. It's essential to note that this is not a bug on my end, but rather a compatibility issue between LibreWolf and fx-autoconfig. I've opened an issue here for those interested in resolving the root cause.
- Enhanced OSK Hide Mechanism: The On-Screen Keyboard (OSK) hide mechanism has been refined to dynamically respond to URL changes. For instance, when searching on a search engine, the OSK overlay will now automatically hide, eliminating the previous awkward behavior that required manual intervention.
For those interested in the technical details of the database injection and to address the security concerns raised by @domubpkm, I've included a flowchart that illustrates the management of the LibreWolf profile. This should provide a clear understanding of the process and help alleviate any concerns.
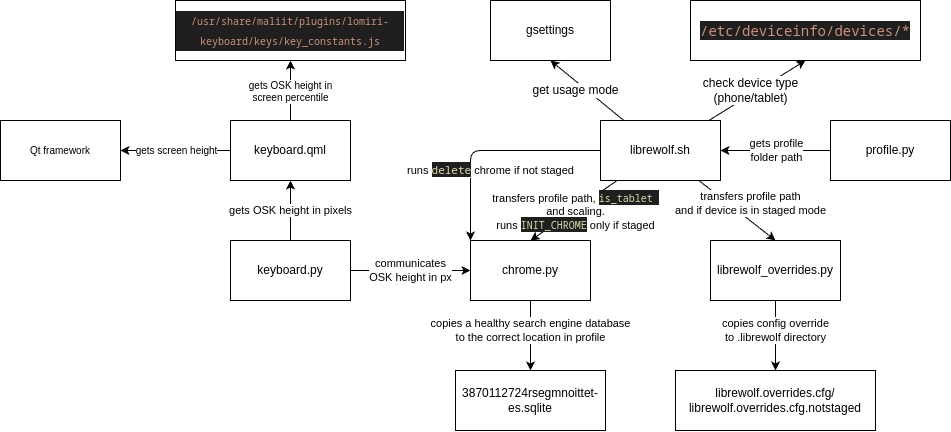
Release: v0.7.11
STATUS: Released on github
Significant updates have been made in the release:
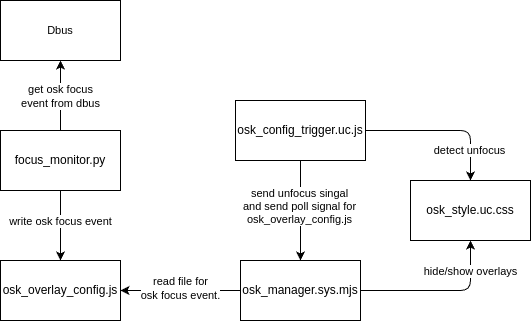
- OSK Dynamic Reactions: The browser detection mechanisms have been replaced with a more robust approach, utilizing a Dbus monitor to listen for OSK focus events. However, this new method has a limitation: the Dbus monitor can only detect when the OSK gains focus, but not when it loses focus. This introduced a challenge in detecting unfocus events, which has been temporarily addressed by implementing a crude solution involving a tinted overlay over the screen. This overlay is active when the OSK overlay is shown, allowing the system to detect when to unfocus.
- Bug Fix: The
is_tabletfunction, which resulted in many crashes in the v0.6.10, has been fixed.
For those interested in a more detailed understanding of the new OSK dynamic reactions architecture, a flow chart is provided.
If you have any questions or would like to discuss the development of uWolf, please don't hesitate to ask in this thread. Your input and feedback are valuable to the project. Feel free to share your thoughts, suggestions, or concerns, and I'll do my best to address them.

