@kugiigi
Yes, and in the past, starting the Bluetooth connection from the system settings/Bluetooth has always given better results.
Posts
-
RE: Call for testing: Ubuntu Touch 24.04-1.2
-
RE: Call for testing: Ubuntu Touch 24.04-1.2
@Moem
Sorry for this.
You could use
journalctl --since "2026-02-09" --grep 'blue' >Downloads/journalctl.log
After that, we will know how to use journalctl. -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@Moem
In fact, I guess it would be better, as gpatel-fr has suggested, to rerun the commands but without the --boot argument to collect the all journal. -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@Moem
Journalctl persists during a long time. -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@Moem
There's always a first time for everything (and a last time, for that matter).
If you connect your phone to your PC through USB (for example, the one you used to install Ubuntu Touch) and open a terminal, you can run the command
adb shell
This will open a remote connection to your phone.
In this connection, you can run the command
sudo journalctl --boot --grep 'blue' >Downloads/journalctl.log
Than you can type exit to return to your local terminal and run
adb pull /home/phablet/Downloads/journalctl.log ~/journalctl.log
This will get the phone's file in your home folder. -
RE: Whatslectron: Whatsapp Web with Electron.
@pparent
Thanks for this.
I have tried and it works too on 24.04-2.x
Voice is working.
But can't be closed. -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@domubpkm
Is it possible (to hide an unknown number and display my first favorite) ? -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@gpatel-fr
It was not only the ringtone, the contact shown in the phone call history is my wife's contact too...
Never saw this.
Same in exPhone history.
It was the last call received previously (yesterday evening) -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@peat_psuwit
I just noticed some strange behaviour on my phone, which is still on RC, that I had never seen before.
At 11:57 a.m., my phone rang, indicating that the call was from my wife, with her personalised ringtone.
My wife's phone was sitting on the kitchen table. She did not call.
Her contact appears in the list of missed calls.
In my received text messages, I have a message saying that the number xxxxxxx called me without leaving a message. It was not my wife's number (nor was it in my contact list, for that matter).
Perhaps it was an accidental glitch...
Exphone app installed. This app has recognized my wife's contact too. -
RE: Call for testing: Ubuntu Touch 24.04-1.2
I am still in RC and the discharge issue has disappeared, for the moment.

-
RE: Call for testing: Ubuntu Touch 24.04-1.2
@peat_psuwit
Not yet returned to 24.04-2.x but without any change of usage, this is a bit more meaningful.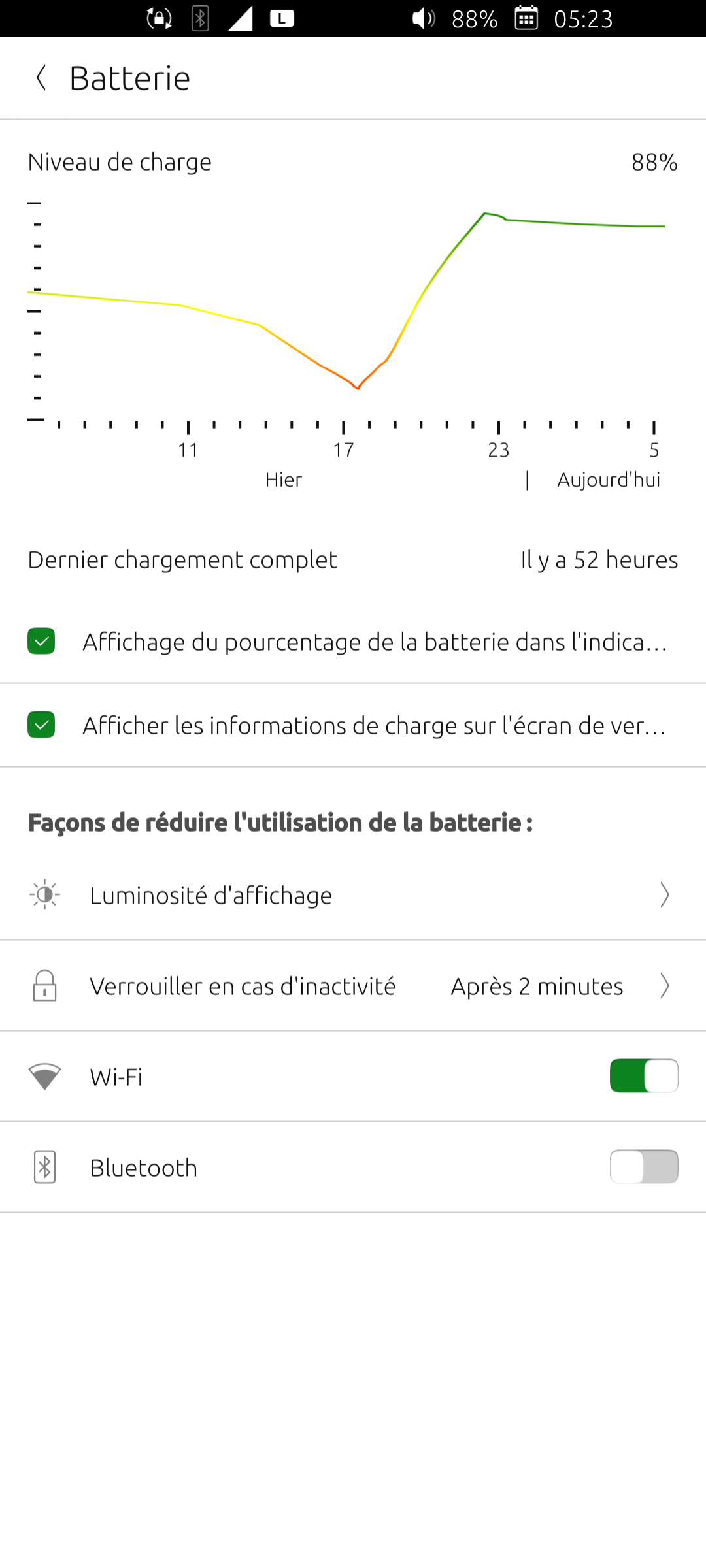 /home/jll/Téléchargements/1/screenshot20260210_052307486.png
/home/jll/Téléchargements/1/screenshot20260210_052307486.png -
RE: Call for testing: Ubuntu Touch 24.04-1.2
@peat_psuwit
Hello.
No issues with usage, but my impression is that the battery drains faster than with the previous version.
Generally, I can go four days without any issues, but currently, in two days, I've gone from 100% to 17%.
Xiaomi Redmi Note 9 Pro (as you know).
How can I objectively assess this? -
RE: Galaxy s21
@Bushman77
To complete Wally's answer, here is what it means:
https://ubports.com/porting -
Interesting presentation at Fosdem 2026. Transferable to UT?
Hello.
I found this presentation showing the adaptation of an open-source Android application ( NewPipe ) to Sailfish OS very interesting.
This could be a way to expand the software library.
https://video.fosdem.org/2026/ub4132/R7NR3U-newpipe-sailpipe.av1.webm -
RE: French ID app interoperability.
@pparent
Hello.
I was wondering if the UBports Foundation could contact one of the members of the European Parliament mentioned in this article to discuss a survival strategy...
(sorry, it's in French... )
)
https://linuxfr.org/news/la-commission-europeenne-publie-une-feuille-de-route-sur-le-logiciel-libre -
RE: Xiaomi Redmi Note 7 (Lavender) Ubuntu 24.04.1 Status
@nparafe
Hello.
Thank you for sharing your experience.
Regarding the noise during calls, which Android ROM was installed on the phone before installing UT? -
RE: Unable To Scan WI-FI Networks (24.04.1-1) on redmi note 9 (merlin)
@lolo
I would say that the ROM depends on the Redmi Note 9 Pro model.
The model is usually printed on the back of the phone under Redmi.
This phone has had many variations depending on where it is sold. (Global, Turkey, India, etc.)
The global model is M2003J6B2G and need joyeuse_global_images_V12.0.3.0.QJZMIXM_20210419.0000.00_10.0_global_0801ff7d09You can get info with
adb shell getprop | grep incremental
adb shell getprop ro.product.nameIn fastboot mode (Power and Volume down until Xiaomi rabbit)
fastboot getvar productTell us wich model and which phone you have and I'll try to find the right ROM to install before install UT.